Changelog
Our Latest Features and Improvements
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Advanced Threat Detection Module
June 1, 2025
Version 4.5.0
Advanced Threat Detection Module & Enhanced Two-Factor Authentication
New Features:
Our new machine learning algorithms detect phishing attempts in real-time, significantly increasing the security of our email systems. This advanced detection system analyzes vast amounts of data to identify patterns and anomalies associated with phishing attacks. It provides immediate alerts to users and administrators, allowing for swift action to prevent potential security breaches.
Additionally, we've introduced enhanced two-factor authentication (2FA) methods to strengthen account security. Users can now choose from multiple 2FA options, including:
- Biometric Authentication: Users can utilize fingerprint scanning, facial recognition, or voice recognition for a more secure and user-friendly authentication process.
- Hardware Tokens: Physical tokens that generate one-time passcodes, providing an additional layer of security that is not susceptible to phishing attacks.
- Push Notifications: Secure push notifications sent to a user’s registered mobile device, allowing for quick and easy approval of login attempts.
- SMS and Email OTPs: One-time passcodes sent via SMS or email, ensuring that even if one method is compromised, the account remains secure through another channel.
These features are designed to provide maximum security with minimal disruption to the user experience, ensuring that your sensitive information remains protected against the latest threats.
Bug Fixes:
We have addressed several critical issues to enhance the stability and reliability of our security platform:
- 2FA Login Process: Fixed an issue where the login process would sometimes fail when 2FA was enabled, particularly under conditions of high server load or network latency. This fix ensures a smoother and more reliable authentication experience for all users.
- Performance Improvements: Resolved performance issues that caused delays in threat detection notifications. These optimizations have reduced the latency between threat detection and alert generation, ensuring that administrators and users are informed of potential threats in real time.
- Data Synchronization: Fixed a bug where user data was not properly synchronized across different modules of the security system, which occasionally led to inconsistent user states and permissions.
- User Interface Enhancements: Improved the user interface to provide clearer instructions and feedback during the 2FA setup process, reducing the likelihood of user errors and improving overall satisfaction.
- Compatibility Fixes: Addressed compatibility issues with various browsers and operating systems to ensure that all users, regardless of their device or software, can utilize the full range of security features without encountering technical difficulties.
- Logging and Reporting: Enhanced logging mechanisms to provide more detailed and actionable insights into security events and system performance, aiding administrators in their efforts to monitor and respond to potential issues.
- Error Handling: Improved error handling to provide more informative messages and recovery options in the event of a failure, helping users to resolve issues quickly and efficiently without needing extensive technical support.
These updates are part of our ongoing commitment to providing the most secure, reliable, and user-friendly security solutions available. We continuously monitor and respond to feedback to ensure that our platform meets the evolving needs of our users and remains at the forefront of cybersecurity technology.
Intrusion Detection & Activity Monitoring
May 15, 2025
Version 4.4.0
Real-Time Intrusion Detection System & User Activity Monitoring
New Features:
Implemented a real-time intrusion detection system that alerts administrators of potential breaches instantly. User activity monitoring now includes detailed reports on login attempts, data access, and file modifications.
Bug Fixes:
Corrected a bug that caused false positives in the intrusion detection alerts. Fixed an issue where user activity logs were not displaying correctly for certain users.
Data Encryption & File Sharing
April 1, 2025
Version 4.3.0
Enhanced Data Encryption & Secure File Sharing
New Features:
Upgraded our data encryption standards to AES-256, providing stronger security for stored and transmitted data. Introduced secure file sharing capabilities with end-to-end encryption.
Bug Fixes:
Fixed an encryption bug that caused errors during data export. Resolved issues with file sharing permissions not being applied correctly.
Security Audits & Compliance
March 1, 2025
Version 4.2.0
Comprehensive Security Audits & Automated Compliance Checks
New Features:
Launched comprehensive security audits that assess system vulnerabilities and compliance with industry standards. Automated compliance checks now support GDPR, HIPAA, and CCPA regulations.
Bug Fixes:
Fixed issues with the audit report generation that sometimes omitted critical details. Corrected compliance check errors that incorrectly flagged certain configurations.
Security Status Indicator
Displays the current security status of your organization with a clear color-coded indicator.
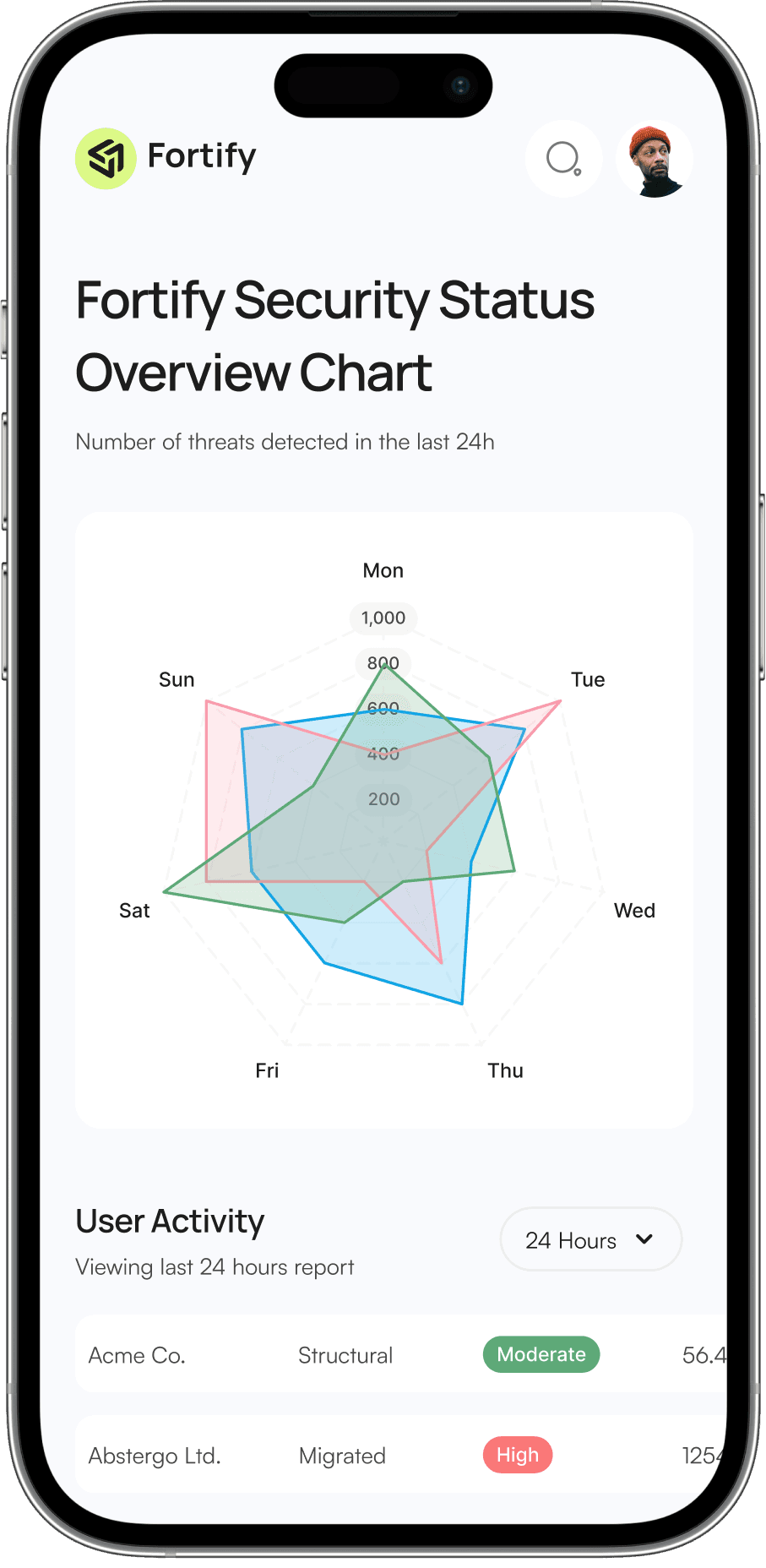
User Activity Monitoring
Highlights the most frequently accessed sensitive files or databases and the users involved, ensuring transparency and control over critical data.
Threat Landscape Overview
Breaks down the threats by type (e.g., phishing, malware, ransomware) to give a detailed overview of the threat landscape.
Data Access Monitoring
Highlights the most frequently accessed sensitive files or databases and the users involved.
Incident Management
Lists the number of active security incidents currently being addressed.
Compliance Monitoring
Our system continuously monitors your network and data environments for any suspicious activities.
Secure Your Data with Fortify Protection Solution
Allows you to set thresholds for security parameters and receive real-time alerts when these thresholds are breached.
Get Started