Key Features
Explore Our Features to Keep Your Data Safe
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Continuously evaluates potential security threats and impact
This includes suggesting security patches, policy updates, and other preventive measures to reduce the likelihood and impact of threats.
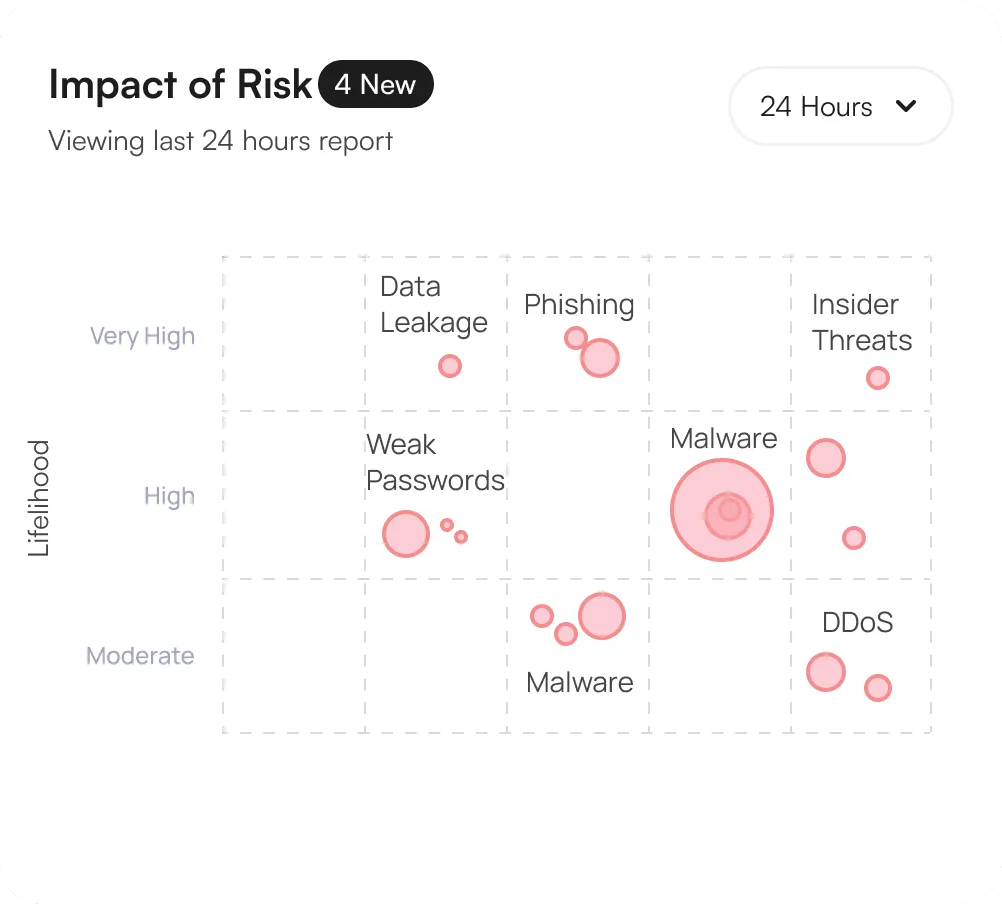
Presents a view of your organization security posture
Allows you to set thresholds for security parameters and receive real-time alerts when these thresholds are breached ensuring you stay informed of critical events.
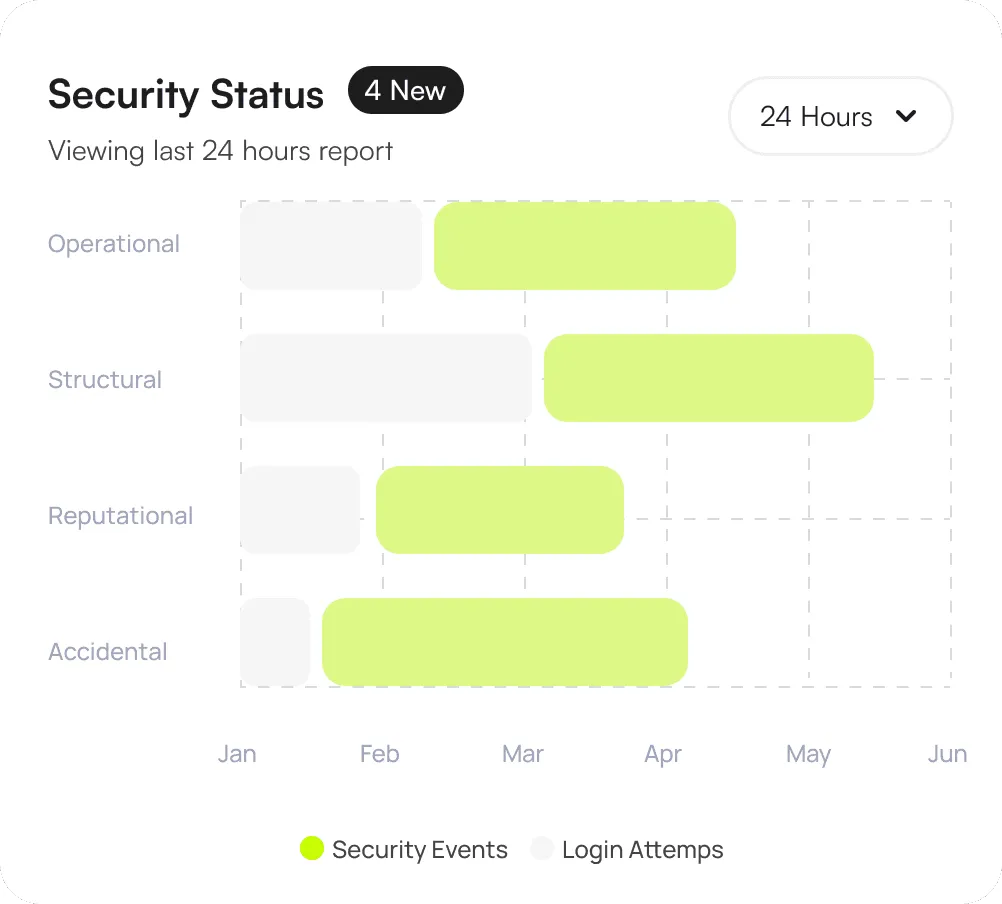
Monitors and logs all the data access events
Monitors and logs all data access events, including who accessed what data, when, and from where. This provides a clear audit trail for compliance and security investigations.
Learn MoreDetails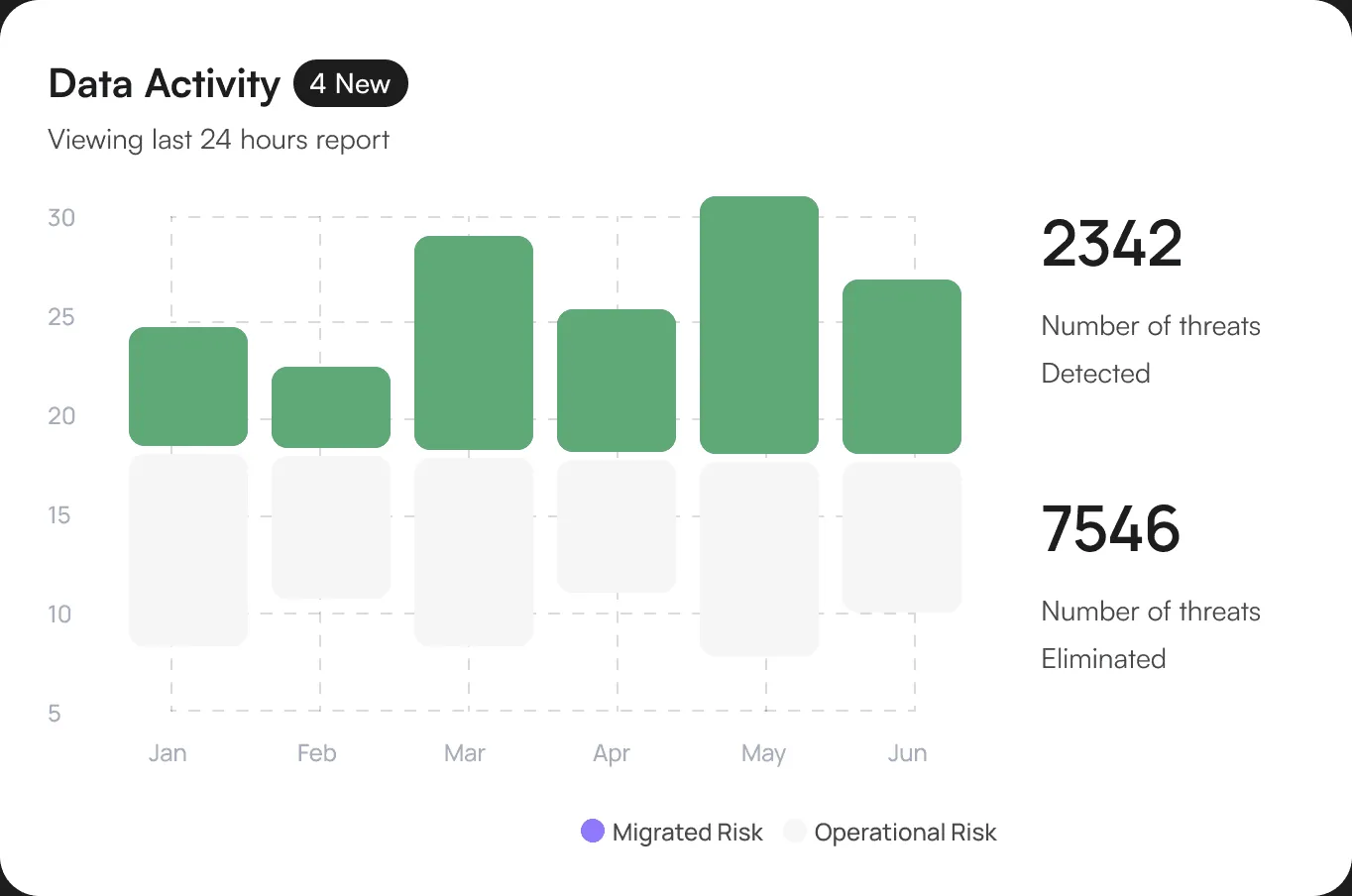
Essential Feature
Discover the Features That Makes Fortify Stand Out.
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
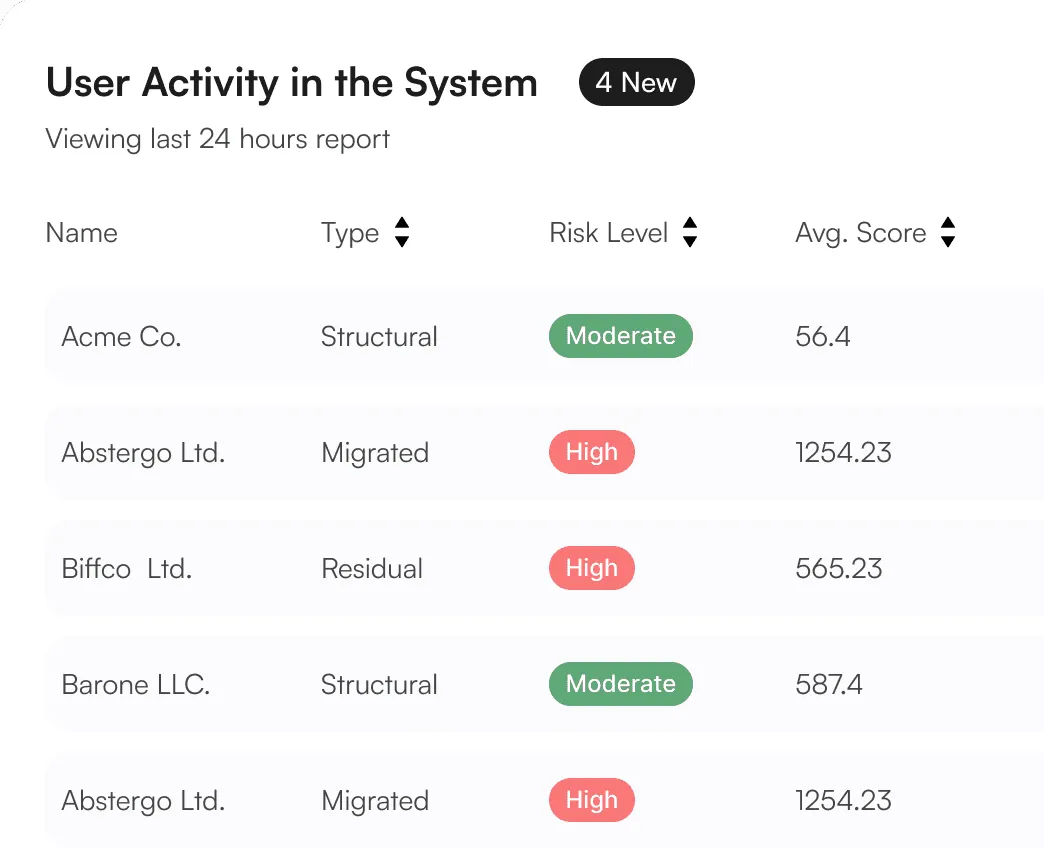
Organize and understand data
Allows you to set thresholds for security parameters and receive real-time alerts when these thresholds are breached ensuring you stay informed f critical events.
Detailed User Logs
Our platform regularly logs all user activities including logins.
Anomaly Detection
This includes unusual login times and access to restricted data.
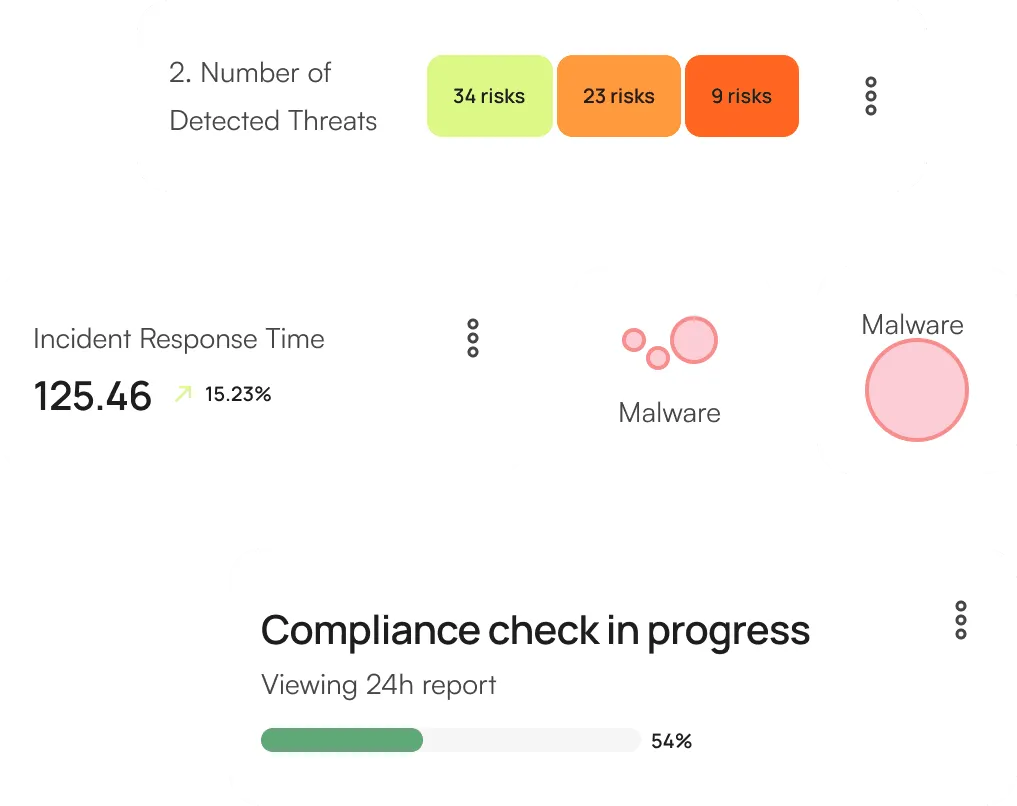
Delivers an all-encompassing security summary.
Our platform ensures that all sensitive data is encrypted both during transmission and while stored
Implement role-based access controls (RBAC) and multi-factor authentication (MFA).
Regularly audit user access to sensitive information and systems to ensure compliance with security policies
Secure Your Data with Fortify Protection Solution
Allows you to set thresholds for security parameters and receive real-time alerts when these thresholds are breached.
Get Started